How to remove rootkits from your computer
Rootkits are a serious threat, a particular form of malware that is often difficult to detect within a computer system and even more difficult to eliminate. Once inside the system, they provide a great deal of power to the hackers who run them, such as permission to access them at will, without the user noticing or being able to do anything to prevent it.
Despite their dangerousness, there are methods that allow their removal in a safe way. Of course, you need to know what to do and how to do it. So here's how to avoid the invasion by rootkits and how to proceed to eliminate them completely from your computer.
Rootkits, a bit of history
The first rootkits appear for the first time in the early 1990s, with the appearance of the first example for the SunOS Unix operating system. And it is precisely from there that it takes its name, given that "root" refers precisely to the system administrator, while "kit" indicates the set of tools necessary to perform the operation on the system.
The first rootkit for Windows , called NTRootkit , came later . The intent of its creator, in this case, however, was quite different. Created by Greg Hoglund , a researcher specializing in information security, it was intended to promote interest in the sector, still under development at the time.
There are also rootkits that affect devices dedicated to the IoT , or the Internet of Things. By now there are more and more smart devices connected to the Internet, so much so that they are starting to be of considerable interest to cybercriminals. All this is due to a dedicated security system still in its infancy, unable to ensure an effective degree of protection.
Rootkits, how they install on computers
Unlike other types of malware, such as " worms ," rootkits are unable to replicate themselves . For this reason they are spread through targeted attacks, such as phishing campaigns, using USB sticks or by downloading files from untrusted sites.
Phishing campaigns are among the most common vectors: through messages that appear to come from trusted senders, they invite you to download files or open links where, waiting for the recipient of the communication, there are droppers . Once installed, these particular programs download the actual malware, infecting the victim's computer. Dissemination via USB memory , on the other hand, sometimes takes place in a more subtle way.
These media can be left in sight so that the victim can be enticed to pick them up, perhaps attached to keys or other media, and use them on their computer to locate the person who may have lost it. By clicking on the files, disguised with other extensions, the infection with the dropper can start.
The last one, however, is the trojan technique. That is, they are rootkits hidden in installation packages of other programs that are downloaded to the computer and infect it when the user starts the file for the first time. Usually, it is pirated software , downloaded from the Internet or from torrent sites .
Rootkits, what happens when they are installed
The typical characteristic of rootkits is that they go deep into the architecture of the system: they nestle in the hardware (to be precise, in the firmware of the components) and not in the software. In fact, droppers usually hide in the BIOS or UEFI . This means that even if you clean your hard drive, the malware still has a chance to self-download, re-infecting your computer in a continuous loop.
To make matters worse, then, there is the ability of this code to block or even remove the security software installed on the machine (because they run long before the operating system and antivirus programs start), as well as exploiting techniques to prevent removal attempts, even if they are detected by antivirus. This is all due to the fact that, to all intents and purposes, rootkits have administrator privileges and, therefore, can potentially perform any operation.
Among the operations that a rootkit can perform are the installation of a backdoor or other malicious software , such as ransomware. Added to this is the reading, copying and deletion of files, changes to system configurations, access to log files and monitoring of keystrokes , for the theft of passwords .

How do you know their presence on your computer?
Unfortunately there is no precise answer to this question but you can still tell from the fact that your antivirus no longer works as before, that your computer crashes much more often and/or seems to stop responding to your commands, that the settings of your operating system have been inexplicably changed, that you are no longer able to open the programs installed on your PC – including your favorite browser – but above all you can notice it from the fact that the speed of your Internet connection seems to be much slower than usual, precisely because of the excessive network traffic caused by the rootkits found on the PC.
How to remove rootkits from PC
There are basically a number of different methods for eliminating rootkits from your PC . The first of these that I advise you to follow is to use TDSSKiller , which is a small free program developed by Kaspersky compatible with Windows XP, Windows Vista, Windows 7, Windows 8.1, Windows 10 and also with other versions of Windows operating systems (both with 32-bit as well as 64-bit variants) with the intention of removing rootkits from your computer.
Once you have downloaded TDSSKiller, to start it (if you want you can also start it in safe mode) there will not even be a need to install it on the PC since it will only be necessary to accept the license agreements and then wait for the program to load:
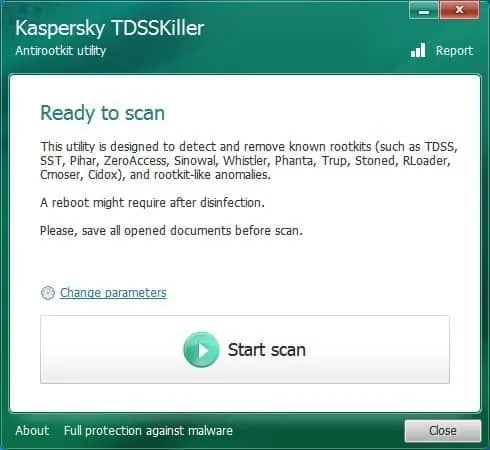
Here's what TDSSKiller looks like once it's started.
Before starting to scan your PC, however, I advise you to click on Change parameters , put a check next to the item Loaded modules , then click on Reboot now , after which you will have to wait patiently for your operating system to load, giving consent to any requests that will be made to you.
At this point you will have to reopen TDSSKiller, press Change parameters again and then tick off all the items in Additional options . Once this is done you can then start a scan of your PC by clicking on the Start scan button.
Before doing this, however, you will need to close any documents and/or files that are still open. Scanning your PC using TDSSKiller will only take a few minutes to complete and, if that's the case, you'll only have to restart your computer again to complete the removal process.
How to remove rootkits from your PC without resorting to TDSSKiller
Another program compatible with Windows XP, Windows Vista, Windows 7, Windows 8.1 and Windows 10 (with both 32-bit and 64-bit versions) that not only allows you to remove rootkits from your PC but also allows you to repair and reinstall any damaged or corrupted system files, it goes by the name of Malwarebytes Anti-Rootkit BETA .
To use Malwarebytes Anti-Rootkit BETA you will only have to download it, extract its contents in any folder, then you will only have to follow the initialization procedure by first clicking on Next , then on Update and then again on Next .
Subsequently, leaving all the various items present ticked, you will simply have to press on Scan , then wait patiently for the scan to complete, and finally click on the Cleanup button in such a way as to remove all the threats detected on your PC (also try not to leave check the Create Restore point item and, if you are asked, restart your computer immediately). Once the PC scan is complete, however, I recommend that you repeat it again in order to verify that all possible existing threats have been completely removed from your PC.
If after restarting the computer there are still other problems, such as the inability to connect to the Internet or the deactivation of Windows Update or Windows Firewall, then you will have to enter the Plugins folder among the extracted files of Malwarebytes Anti- Rootkit BETA, run the fixdamage file, and finally restart your operating system again.
So at this point you should have finally eliminated all rootkits from your PC.
Another tool that gets rid of rootkits is McAfee Rootkit Remover . This program can also be started immediately to clean up the system.
McAfee Rootkit Remover is easy to use and allows you to get rid of complex rootkits and malware.
How to avoid rootkits
Since more or less always the same techniques are used to install rootkits on the PC as are also used to spread common viruses, to avoid contracting rootkits, adware, spyware and other unwanted software again, just follow the usual advice on security, that is:
- always install the latest updates available, both for your operating system and for your antivirus/antimalware;
- use an appropriate firewall, both the software one and, if necessary, also that of the modem router;
- avoid browsing particularly dangerous sites, such as pornographic sites, sites for downloading copyrighted material, chat sites, video chat sites, and so on;
- download programs only from reliable sources, for example from the official website of the software manufacturer;
- never open spam messages, install only genuine software, and, at the same time, install only software that is really needed.
However, if by observing these tips you should find yourself dealing with the dreaded rootkits again, at this point you should still have finally figured out how to eliminate rootkits from your PC .
When you subscribe to the blog, we will send you an e-mail when there are new updates on the site so you wouldn't miss them.
By accepting you will be accessing a service provided by a third-party external to https://www.insightadv.it/


































































Comments